k8s部署Ingress并创建规则的详细介绍
目录
- 一、Ingress介绍
- 二、Ingress文件获取
- 1.1 、说明
- 1.2 、文件内容
- 三、k8s应用 ingress-controller.yaml
- 四、创建Ingress规则
- 五、应用文件
- 六、访问
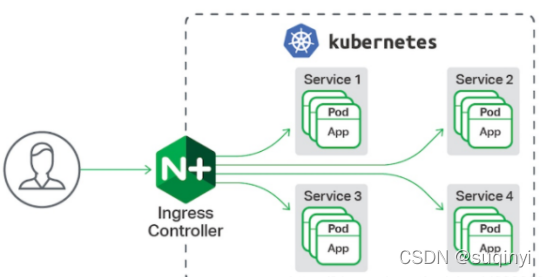
一、Ingress介绍
Ingress由两部分组成:Ingress controller和Ingress服务- 通过 Service 发现 Pod 进行关联。基于域名访问
- 通过 Ingress Controller 实现 Pod 负载均衡
- 支持 TCP/UDP 4 层负载均衡和 HTTP 7 层负载均衡
底层实现是nignx

二、Ingress文件获取
1.1 、说明
官方地址:https://github.com/kubernetes/ingress-nginx
部署文件说明
## 这个地址被墙,需要科学上网!!! # mandatory.yaml为ingress所有资源yml文件的集合 # 若是单独部署,需要分别下载configmap.yaml、namespace.yaml、rbac.yaml、service-nodeport.yaml、with-rbac.yaml wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/static/mandatory.yaml # service-nodeport.yaml为ingress通过nodeport对外提供服务,注意默认nodeport暴露端口为随机,可以编辑该文件自定义端口 wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/static/provider/baremetal/service-nodeport.yaml
1.2 、文件内容
ingress-controller.yaml
apiVersion: v1
kind: Namespace
metadata:
name: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
name: nginx-configuration
namespace: ingress-nginx
name: tcp-services
name: udp-services
kind: ServiceAccount
name: nginx-ingress-serviceaccount
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRole
name: nginx-ingress-clusterrole
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
verbs:
- list
- watch
- get
- services
- "extensions"
- ingresses
- events
- create
- patch
- ingresses/status
- update
kind: Role
name: nginx-ingress-role
- namespaces
resourceNames:
# Defaults to "<election-id>-<ingress-class>"
# Here: "<ingress-controller-leader>-<nginx>"
# This has to be adapted if you change either parameter
# when launching the nginx-ingress-controller.
- "ingress-controller-leader-nginx"
kind: RoleBinding
name: nginx-ingress-role-nisa-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
subjects:
- kind: ServiceAccount
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
kind: ClusterRoleBinding
name: nginx-ingress-clusterrole-nisa-binding
kind: ClusterRole
apiVersion: apps/v1
kind: DaemonSet
name: nginx-ingress-controller
spec:
selector:
matchLabels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
template:
metadata:
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
annotations:
prometheus.io/port: "10254"
prometheus.io/scrape: "true"
spec:
hostNetwork: true
serviceAccountName: nginx-ingress-serviceaccount
containers:
- name: nginx-ingress-controller
image: siriuszg/nginx-ingress-controller:0.20.0
args:
- /nginx-ingress-controller
- --configmap=$(POD_NAMESPACE)/nginx-configuration
- --tcp-services-configmap=$(POD_NAMESPACE)/tcp-services
- --udp-services-configmap=$(POD_NAMESPACE)/udp-services
- --publish-service=$(POD_NAMESPACE)/ingress-nginx
- --annotations-prefix=nginx.ingress.kubernetes.io
securityContext:
allowPrivilegeEscalation: true
capabilities:
drop:
- ALL
add:
- NET_BIND_SERVICE
# www-data -> 33
runAsUser: 33
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
fieldPath: metadata.namespace
ports:
- name: http
containerPort: 80
- name: https
containerPort: 443
livenessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 10
readinessProbe:
kind: Service
#type: NodePort
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
- name: https
port: 443
targetPort: 443
三、k8s应用 ingress-controller.yaml
应用
kubectl apply -f ingress-controller.yaml
如图:

查看是否完成
kubectl get pods --all-namespaces

四、创建Ingress规则
如果没有部署和服务==>查看k8s部署并映射tomcat8
查看自己创建的服务,以tomcat8为例
kubectl get all
自己创建文件 ingress-tomcat8.yaml
vi ingress-tomcat8.yaml
ingress-tomcat8.yaml规则内容
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: web
spec:
rules:
- host: k8s.tomcat8.com
http:
paths:
- backend:
serviceName: tomcat8
servicePort: 80
如图:

五、应用文件
kubectl apply -f ingress-tomcat8.yaml

六、访问
1.本地测试用域名会访问不到,所以要配置下本地hosts文件
hosts文件位置:C:\Windows\System32\drivers\etc\HOSTS
如图:

不带端口访问,直接使用域名

使用ip端口访问的效果
到此这篇关于k8s部署Ingress并创建规则的文章就介绍到这了,更多相关k8s部署Ingress内容请搜索我们以前的文章或继续浏览下面的相关文章希望大家以后多多支持我们!
赞 (0)

